
Cloudflare is a cloud-based service that provides security features like SSL and DDoS protection, visibility into the traffic to your website, and scalability features such as CDN and page caching. WP Engine recommends Cloudflare when configuring DNS because Cloudflare offers CNAME flattening for free. In this article we explain when to use Cloudflare, how to configure their services, and how to troubleshoot any conflicts that arise.
Cloudflare and CNAME flattening
WP Engine recommends CNAME records for DNS – a CNAME allows you to point a domain (domain.com or www.domain.com) to another domain, instead of an IP address. This is important because it allows you to point your domain to your environment.wpengine.com URL, which WP Engine will automatically configure to point to the correct server environment.
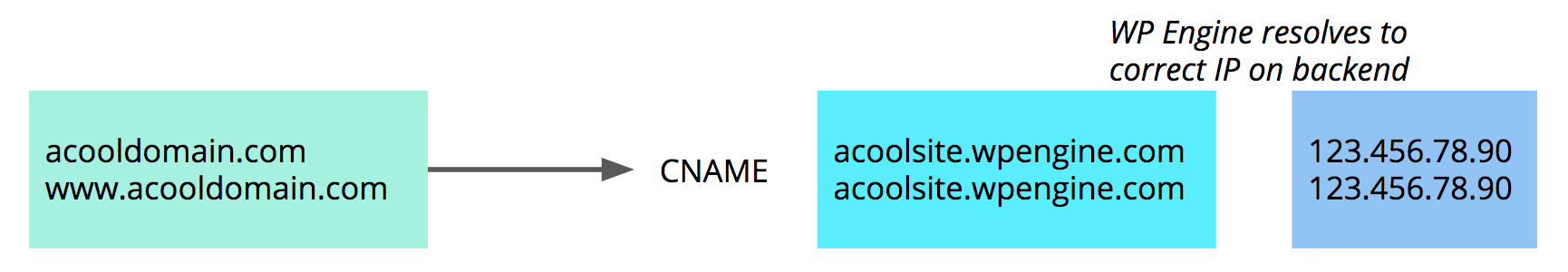
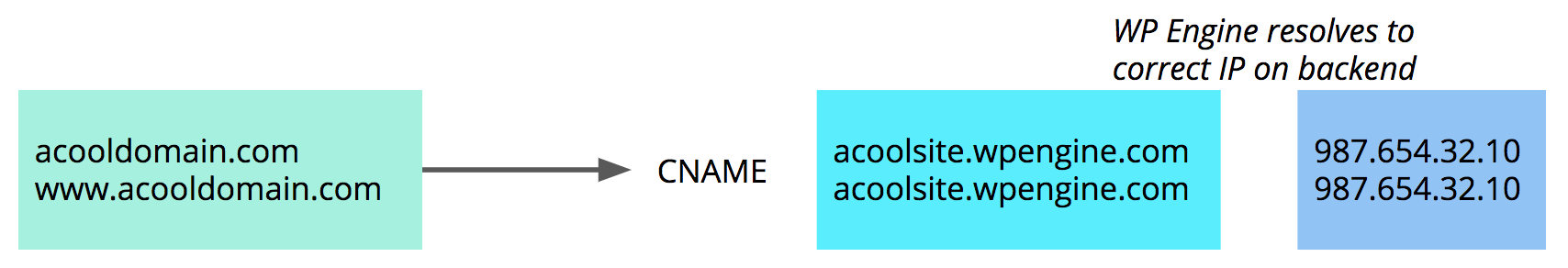
If your website is ever migrated to new server hardware, the backend IP address will change. But if you are pointing to WP Engine via CNAME, we will manage the change for you automatically on the backend.
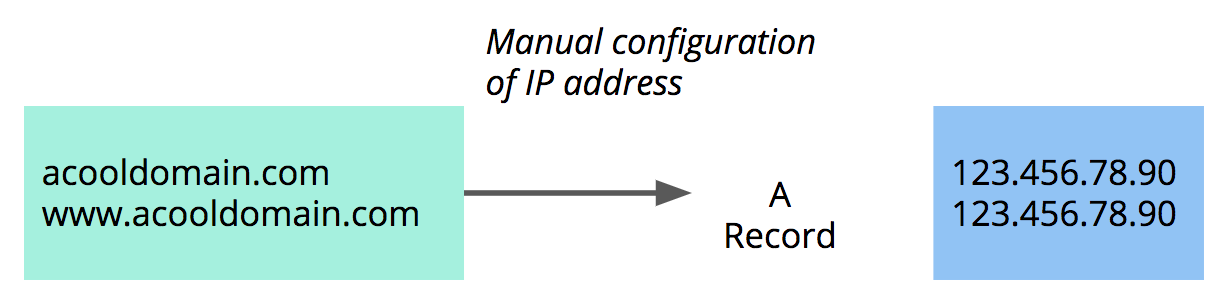
Some users choose to point directly to an IP address (via an A record).
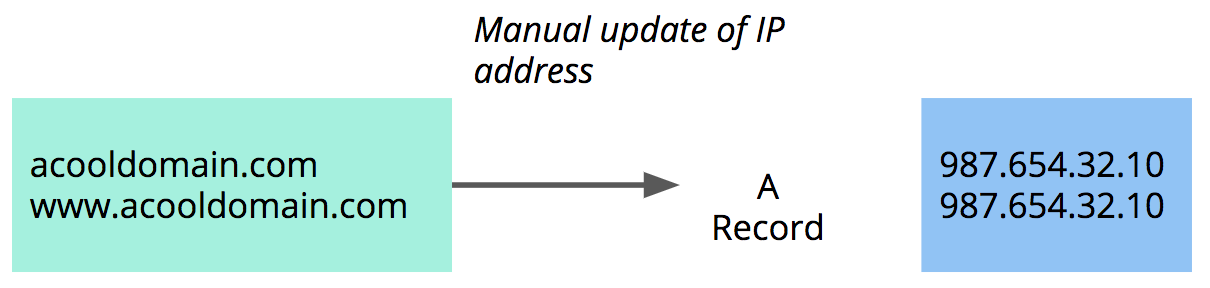
If you choose to point to an IP address directly, you will need to manually update this record anytime WP Engine migrates you to newer and more efficient server hardware.
CNAME records help by ensuring you don’t have to make updates in case of a server migration. Trouble is, most DNS registrars do not offer the ability to configure a CNAME record for your root domain (domain.com), only for your “www” record (www.domain.com). This is why CNAME flattening through Cloudflare is attractive. Cloudflare offers free plans that support CNAME flattening, in addition to powerful features like SSL, CDN, and more.
Head to our guide, Configuring DNS for WP Engine for a guide on DNS records, as well as links to guides for configuring DNS for the most widely-used DNS registrars.
Cloudflare and SSL/TLS
Cloudflare offers several SSL/TLS options for encrypting the user data entered on your website. However, WP Engine also offers free Let’s Encrypt SSL/TLS certificates for your website. In this section we will explain how to configure your SSL/TLS settings in Cloudflare in a way that will not interfere with your WP Engine settings.
Before continuing, please note that Cloudflare SSL enablement can take up to 24 hours for free Universal SSL, but will be enabled instantly for dedicated/paid SSL offerings.
If you do not have an SSL certificate with WP Engine
If you have not added a WP Engine SSL or installed a 3rd-party SSL certificate through the WP Engine User Portal, you may use the following SSL options from Cloudflare:
Universal SSL: Flexible. This option (available on the free Cloudflare plan) encrypts traffic between the end-user’s web browser and Cloudflare, but not the connection between Cloudflare and your WP Engine web server.
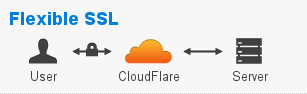
source: cloudflare.com
Off. This option does not encrypt traffic between the end-user’s web browser and Cloudflare, OR the connection between Cloudflare and WP Engine. Use only when you do not want to encrypt user data, and when you wish to access your website via http://domain.com instead of https://domain.com.
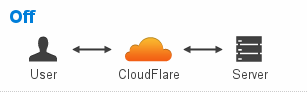
source: cloudflare.com
If you do have an SSL certificate with WP Engine
If you have added a WP Engine SSL or 3rd-party SSL certificate through the WP Engine User Portal, you may use the following SSL options from Cloudflare.
Remember: Cloudflare’s free Universal SSL feature takes up to 24 hours for propagation. If you have installed an SSL certificate through WP Engine prior to configuring Cloudflare, make sure the Status shows as “Active” under the Crypto section of the Cloudflare dashboard before pointing the Nameservers for your domain to Cloudflare. This will ensure you do not encounter SSL errors during propagation.
Universal SSL: Full (Strict). This option is preferred if you have a valid SSL certificate installed via the WP Engine User Portal. This will encrypt the connection between your end user and Cloudflare, as well as the connection between Cloudflare and WP Engine.
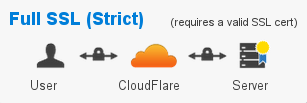
source: cloudflare.com
Universal SSL: Full. This option should only be used if you have a self-signed or otherwise invalid SSL certificate installed via WP Engine. This option is the same as “Full (Strict)” in that it requires an SSL to be installed at WP Engine, but it allows users to bypass the authenticity check of the SSL certificate.
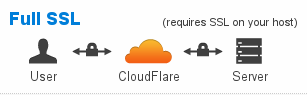
source: cloudflare.com
Strict (SSL-Only Origin Pull). This option is only available for Enterprise-level plans with Cloudflare. It will encrypt connections between the end user and Cloudflare, as well as the connection between Cloudflare and WP Engine. However, this option has the added benefit of redirecting HTTP requests to HTTPS when HTTP is requested.
Do not use the Disable Universal SSL option. This will prevent your WP Engine SSL from working properly.
Purchasing an SSL Certificate from Cloudflare
Cloudflare also offers the option to purchase a “Dedicated SSL” in their dashboard for all plans. This SSL certificate will encrypt the connection between your end user and Cloudflare, but offers a better experience by showing your domain instead of a default Cloudflare one.
With Cloudflare free Universal SSL, your certificate will appear in this way in Chrome:

source: cloudflare.com
Note that the domain is a default “cloudflaressl.com” URL. This is because with the free Universal SSL option, Cloudflare combines your domain with several others into its free offering. If you use Cloudflare SSL and WP Engine SSL, your Cloudflare SSL will be the one that shows to users when they inspect the certificate. If you wish to display only your own domain with the certificate from Cloudflare, a dedicated SSL from Cloudflare is required.
With Cloudflare Dedicated SSL, your certificate will appear in this way in Chrome:
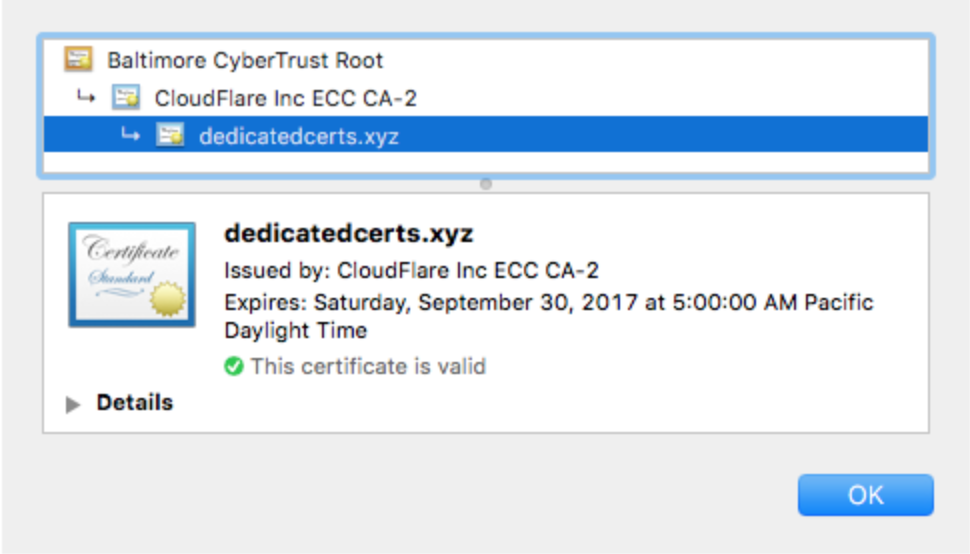
source: cloudflare.com
Note the use of a custom domain in the SSL certificate. This is the defining difference between Cloudflare Dedicated and Cloudflare Universal SSL offerings.
Once your Cloudflare Dedicated SSL certificate has been purchased, you will have the same configuration options described in the sections above.
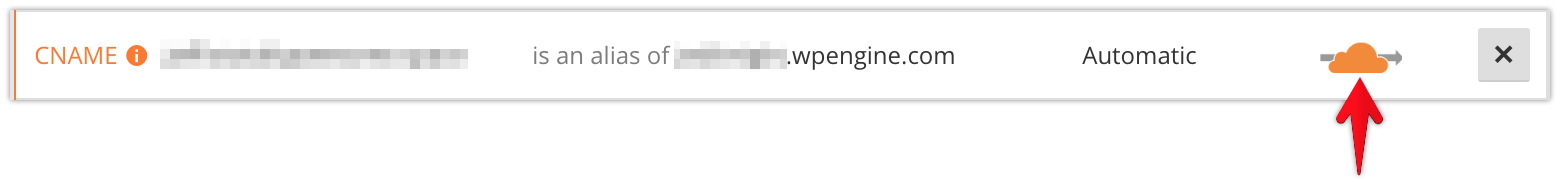
If you want your WP Engine SSL certificate to appear instead, you will need to use Cloudflare in “pass-through” mode. This means you will forego the CDN services of Cloudflare and use it only as a CNAME flattening DNS service. To do this, click the orange “cloud” icon next to your domain on the “DNS” page.
Custom SSL Certificates
If you wish to upload your own SSL certificate to Cloudflare, perhaps one purchased through a 3rd-party SSL certificate provider, this requires a Business-level plan with Cloudflare. With this method you can upload the same certificate to WP Engine (requires Growth plan or higher) and Cloudflare for encryption of user data.
Troubleshooting Cloudflare SSL
You may encounter issues such as errors or redirect loops if your Cloudflare SSL settings are not configured correctly. Be sure to refer to the above options for guidance when configuring your Cloudflare SSL. If you experience further issues, look to Cloudflare’s SSL troubleshooting article for more troubleshooting steps.
Cloudflare CDN
Cloudflare also offers free CDN (Content Delivery Network) services for static files like images, JavaScript, and CSS styles. View a full list of the file extensions served from Cloudflare CDN.
A CDN helps you serve a global audience more quickly. CDN copies your website’s images, styles, and JavaScript, and caches them on a network of global servers. When a user from the other side of the world requests your page, these files will be served to them more quickly because a CDN server is close by. Cloudflare is a “zero configuration” CDN service, meaning it is automatically enabled when you activate Cloudflare on any plan level.
WP Engine includes CDN in its plan offerings as well. When WP Engine enables CDN it rewrites the static files like images, CSS styles, and JavaScript in your source code to the CDN URL. Because of this, your resources may not use Cloudflare CDN when WP Engine CDN is enabled. If you prefer the Cloudflare CDN service, ensure your WP Engine CDN is turned off in your User Portal under Utilities.
Cloudflare Speed Options
Cloudflare has a suite of features available to help improve your website’s speed under the “Speed” tab. In this section we will cover explain how Cloudflare speed options work with WP Engine.
Auto Minification
Minification is the practice of removing extra white spaces, comments, and line breaks that make your code more readable for developers, in order to make it easier and faster for a web browser to interpret. Auto minification will minify HTML, CSS, and JavaScript files by default. Keep in mind, auto minification cannot minify files from third-party domains (such as your Google Analytics script), and will not minify files that already have “.min” in the file name. These are files which have already been minified.
While auto minification has not been known to cause conflicts with WP Engine, keep in mind that optimization plugins like Autoptimize or BWP Minify may already be combining and minifying your files for you. When Cloudflare encounters these files, it skips auto-minification because the files are already minified.
Railgun
Railgun is a compression service which compresses the web pages dynamically generated on your origin server. WP Engine does not support installation of Railgun at this time. Railgun is unsupported because installation involves opening a port and installing the railgun service on the server.
Rocket Loader
Cloudflare’s Rocket Loader script bundles JavaScript files together so that web browsers can receive all JavaScript files with a single HTTP request. It also asynchronously loads JavaScript files so they do not block the rendering of your page (also known as “Defer the Parsing of JavaScript” to some web page testing services). You can select “Automatic” optimization, meaning all scripts will be loaded asynchronously. Or, select “Manual” to self-select which scripts should be optimized and which should load as-is.
Rocket Loader has no known conflicts with the WP Engine platform itself, but it is important to be aware that some scripts may not work properly when loaded asynchronously. If you enable this setting and notice odd behavior on your website, try “Manual” configuration instead. If you are still unable to get a working configuration manually, using Autoptimize or BWP Minify for asynchronous loading of JavaScript may work better.
You will see the Rocket Loader script when viewing the source code of your web page like so:
<script type="text/rocketscript" data-rocketsrc="https://mydomain.com/wp-includes/js/jquery/jquery.js?ver=1.12.4">CloudFlare Cache
Cloudflare caches your website’s static files by default on its network of edge servers. This helps deliver your website content to your visitors around the world quickly, by serving them the assets from the edge server closest to them. You can configure cache settings for these static resources on the “Caching” section in your Cloudflare dashboard, as well as purge specific files or all files from Cloudflare cache.
By default, Cloudflare does not cache full web pages, but you may set a page rule for this if you prefer. If you wanted Cloudflare to cache all pages, you could use the following setting:
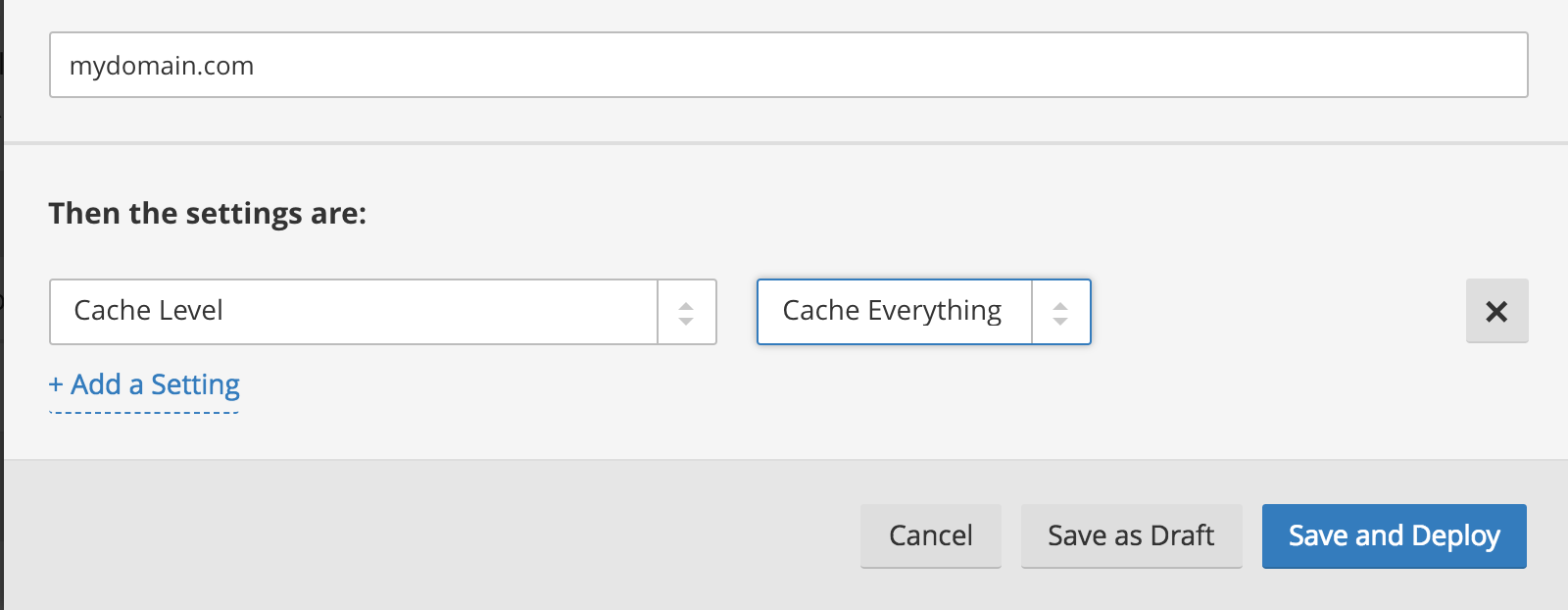
If you use WP Engine in combination with Cloudflare, then Cloudflare will hold each web page in cache for 10 minutes (reading our cache expiration headers) as a default using the “Cache Everything” setting, and static files for 30 days. However, Cloudflare also has an “Edge Cache expires TTL,” meaning it will only look for new content to cache from WP Engine when the edge cache expires. For the free plan tier, the default “Edge Cache expires TTL” is 2 hours, while other plans have lower expires TTL options.
Below is the list of the lowest expires TTL options by plan type.
| Plan | Lowest edge cache expires TTL |
| Free | 2 hours |
| Pro | 1 hour |
| Business | 30 minutes |
| Enterprise | As low as 30 seconds |
If you have made changes to a page or added a new resource and are not seeing the change within 10 minutes, try purging the WP Engine cache first. If this does not help, try purging the Cloudflare cache from the “Caching” section. And, to rule out conflicts with Cloudflare altogether, try using a Host File Trick to view your website directly from WP Engine’s servers.
For more information on Page Rules including caching options, check out Cloudflare’s page rules tutorial.
Development Mode
Last, if you are testing file or page changes, or troubleshooting errors, placing Cloudflare in Development Mode can be an easy way to determine the source of the issue. Development Mode enables “pass-through” mode on Cloudflare, meaning it simply passes all requests on to your origin server (WP Engine). If you are experiencing an issue that goes away when Cloudflare Development mode is on, this indicates an issue with Cloudflare settings or caching.
To enable Development Mode, visit the “Caching” page in your Cloudflare dashboard and select Development Mode. The Development Mode setting will automatically bypass Cloudflare’s cache for three hours, before turning the setting off again. Please note: Development Mode does not purge edge cache. As a best practice you should enable Development Mode and purge edge cache when troubleshooting.
DDoS Mitigation
Cloudflare’s platform offers some key security benefits as well. In particular, when pointing your nameservers to Cloudflare, you are obscuring the “origin IP address” from bad actors. This means they cannot target the source of your website’s content (WP Engine) in a DDoS (distributed denial of service) attack. DDoS attacks are targeted attacks intended to take down your website by flooding it with bad requests. By nature, Cloudflare obscures your origin IP with any plan, which is a good step to prevent DDoS attacks. However, Cloudflare has additional settings you can configure to help mitigate a DDoS should you encounter this scenario.
I’m under attack mode, found in the Firewall > Security Level settings on Cloudflare, tells Cloudflare to challenge visitors to your website using Javascript. Users will see an intermediary page while their validity is verified by Cloudflare for a brief few seconds, before continuing to your website. This allows Cloudflare to sort out the bad actors and only allow real visitors through to your website.
High security mode in the same location will not challenge all users, but will present the JavaScript challenge page to visitors with threatening behavior in the last two weeks.
You can adjust these firewall settings as needed to prevent attackers, botnets, and DDoS attempts from reaching your WP Engine server.
Please note: It is far easier to use Cloudflare from the start as a preventative solution to DDoS attacks, than to try to implement DDoS protection while currently under attack. We recommend pointing your Nameservers to Cloudflare when initially configuring your DNS, for easy mitigation of DDoS if ever needed.
Enabling Cloudflare during a DDoS attack
If you need to enable Cloudflare while currently under DDoS attack, the mitigation strategy is more difficult. Because Cloudflare was not enabled from the start, attackers were likely able to find your “Origin IP,” meaning they can direct the attack on your WP Engine origin server, bypassing Cloudflare. With that in mind, you will need to point your Nameservers to Cloudflare and enable “I’m under attack” mode.
If this alone does not begin to mitigate the DDoS and your website is still inaccessible, you may need to enable the Cloudflare WAF as well, which comes with any paid plan. WP Engine Support will work with you to monitor the situation and offer further troubleshooting steps if needed.
Other traffic solutions
Beyond mitigating DDoS from many vectors, Cloudflare also allows you more granular control over your website’s visitors and uptime.
Always online is a feature found in the “Caching” page of the Cloudflare dashboard. This feature allows Cloudflare to serve a cached version of your website even in the event of downtime, or errors. The “always online” feature is enabled by default, but may be turned off if you wish.
Firewall access rules and User Agent blocking can be configured from the “Firewall” page in the Cloudflare dashboard. These rules can be used to block known bad IP addresses, countries, and user-agents, or to allow known good IP addresses, countries, and user agents. This is your “whitelist/blacklist” or “challenge” configuration tool on Cloudflare.
Challenge Passage is also configured under “Firewall,” and is the setting that controls how long a JavaScript challenge is accepted. After the allowed window of time, users will be challenged again.
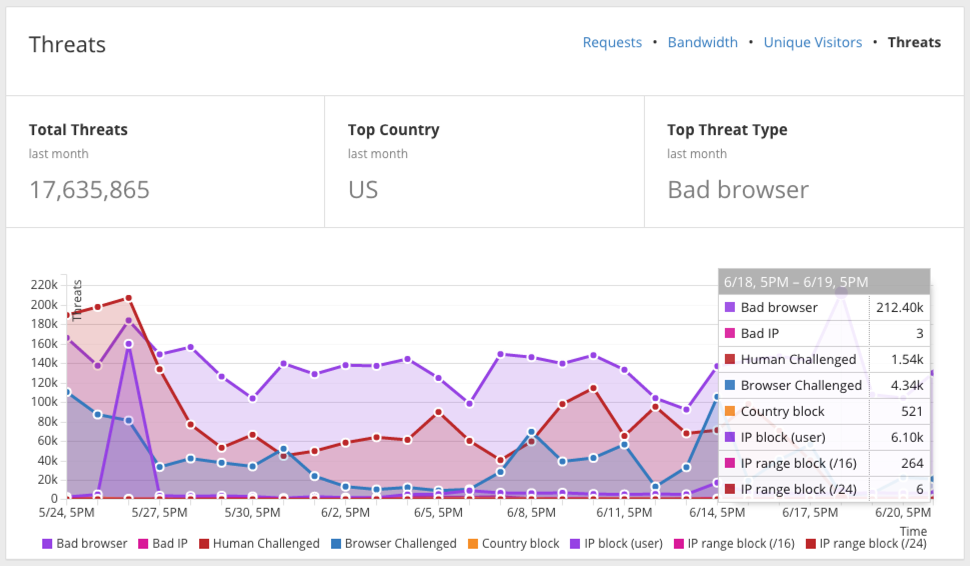
Threat Analytics can be found in the “Analytics” page of the Cloudflare dashboard. This page will help you determine how often threats are detected, from which IP addresses and countries the threats originated, and how the above settings are performing against these threats. Learn more about Cloudflare analytics.
Cloudflare WordPress Plugin
Cloudflare offers a WordPress plugin with easy one-click configuration settings for WordPress. When you select the “Optimize Cloudflare for WordPress” option, the following settings are configured automatically:
| Setting | Value |
| Security level | Medium |
| Caching level | Standard |
| Auto Minify | Enable Auto Minify for JS, CSS, and HTML |
| Browser Cache Expiration | 4 hours |
| Always Online | On |
| Development Mode | Disabled |
| IPV6 Compatibility | Off |
| WebSockets | On |
| IP Geolocation | On |
| Email Address Obfuscation | On |
| Server-side Excludes | On |
| Hotlink Protection | Off |
| Image optimization (Polish and Mirage) | Off (unless on Pro or higher plan) |
| Rocket Loader | Off |
Additionally, you will be able to configure WAF settings if you have a paid Cloudflare plan (Pro and higher). Within your WordPress Admin Dashboard you can also edit cache settings, security level, and “always online.” Last, you have the ability to view your website analytics like threat detection, bandwidth, and more directly through the Cloudflare plugin.